Writing
Starting a Startup
I've never wanted an ordinary life. It's why I did a PhD at 24 instead of entering the workforce like all of my friends. It had a negative affect on my careers prospects, LMAO (surprise). My topic was on the history of Western Philosophy and why we became rational...
What The Actual (Fuck) is Blockchain?
The idea for blockchain came from a now germinal paper written in 2008 by the man known as Satoshi Nakamoto, what his or their real name is, no-one knows which just adds to the mystery and intrigue around the whole community. Nakamoto referred to "blocks" and "chains"...
King Root
Since 1983 there has been more than one way to make a connection an intricate dance called a three-way handshake one way to ask for permission one way back to ensure what we have is stable another to acknowledge our transmission this is the language written from every...
It’s Hammertime: SQL Injection For Beginners
Oh hey! I presented at the Australian Information Security Association (AISA) Conference in 2019 with a presentation called SQL Injection for Beginners: It's Hammertime. Peeps asked for the slides so here they are as a YouTube experience with all the vids and giph's...
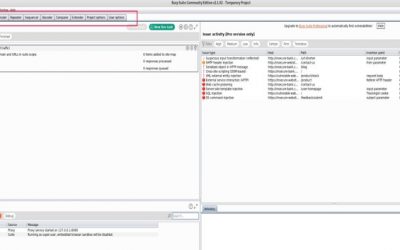
Burp: A Quick Installation Guide
In order to execute a SQL injection, for example, we need to see what’s going on in the code behind the interface when we enter our username and password and send it over the internet or from the login page to the database. To do that we need to use...
W0m3nWh0HackM3lb0urn3: Monthly Ethical Hacking Sessions
W0m3nWh0HackM3lb0urn3 is a safe space for women who are keen to learn to ethically hack. We are a community of women identified hackers who support each other to increase our skills and hack all the (legal) things. Why? There’s a worldwide shortage of skilled cyber...
Penetrating Real-Time Threat Behaviour: Cyber Analytics and the Pen Tester
It’s the wild, wild, west out there in cyberspace, except the feral camels[1] that once roamed Texas are the hackers, and they’re roaming beyond borders and through firewalls on the daily. At present, cyber threat intelligence gathering is a mish-mash of intrusion...
Kneel
I’ve knelt down and opened my mouth to check the heart beat of many women it lives there louder than the organ that sustains us but only this time have I opened my heart wider than my legs and said I love you for the way you make my eyes widen before our lips...
The era of Lesbian Bed Death is over, long live Lesbian Fuck Eye
Sex is an art. And one that lesbians in particular have apparently, according to myth, taken a few decades to get their heads and legs around. Let alone actually in their beds. Today however, lesbian women have more orgasms, better sex and sex that lasts longer than...
WTAF is IoT?
From space, to transport, to the design of cities, IoT is the latest acronym to sweep the cyber landscape. IoT is short for Internet of Things and was coined by Kevin Ashton in 1999. IoT is any device, be it your phone, laptop or Raspberry Pi that is connected to the...
Searching Twitter Data with R and Grep
Learning how to use R Studio, R and then all the libraries and functions inside it can be hell(ish). But there's good little ways to search your Twitter data for whatever you're looking for, and give you some instant satisfaction in the process. Step 1 You will need...
Lesbian Desire Across The Ages: From Insane To Cult Hero
Cast your mind across everything you know about lesbians in history. In particular, Australian history. You might be able to name one or two lesbians, bisexuals or queer women from the 1900s, if you’re in the know. Otherwise, it’s a pretty bleak and sparse canvas,...